
While some government mandates and Internet standards organizations have made a call for DNSSEC, only a small percentage of domains are DNSSEC signed. Only 56 domains out of 1518 domains (3.7%) were DNSSEC signed with a chain of trust in our comprehensive September 2019 study of the 100 largest global banking institutions as listed in the 2018 S&P Global Bank ranking. The total list of domains also includes subsidiaries, past bank names, registered typo names, and acquired banks. (We also do studies on Fortune 500 domains and US government domains.)
Of these banking institutions, 16 out of 100 had at least one DNSSEC-signed and validating domain. (But note this doesn't imply that their main domains are signed.) Two other banks had domains with DNSSEC signatures but without a chain of trust. None of the banks in this study had all of their domains signed. This report shares a small analysis as part of our ongoing DNS research and comprehensive DNS operations checks.
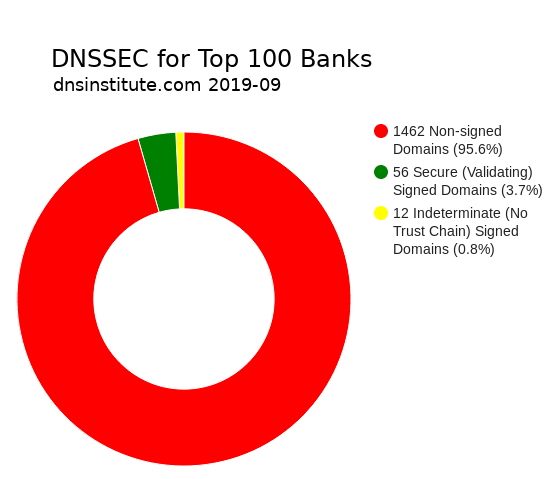
68 domains had DNSSEC signatures, but twelve didn't have a chain of trust (their parents didn't know about their DNSSEC setup). The banks with signed but unvalidated domains (indeterminate) include: Barclays PLC, Oversea-Chinese Banking Corp. Ltd., Société Générale SA, State Bank of India, and Svenska Handelsbanken AB.
Of the signed domains, none were signed prior to September 1. Most of the signatures expire by mid October, with one outlier: CaixaBank had a domain with a 180 day validity period. A few didn't follow best practices: Oversea-Chinese Banking Corp. Ltd had a domain with a validity period of only two days. And Barclays PLC, BNP Paribas SA, ING Group NV, and Oversea-Chinese Banking Corp. Ltd. had domains with signatures which expired in less than three days.
The algorithms used include:
1 ECDSAP384SHA384
1 RSASHA512
4 RSASHA1NSEC3SHA1
5 ECDSAP256SHA256
11 RSASHA1
57 RSASHA256
The counts total more than 68 because some domains used multiple algorithms. 63 of the 68 signed bank domains used a non-recommended RSA algorithm.
Of those using RSA algorithms, eight domains used a 2048 bit key size. 55 domains used the non-recommended 1024 bits; these include domains for Bank of America Corp., Barclays PLC, BNP Paribas SA, CaixaBank SA, Capital One Financial Corp., Danske Bank A/S, Deutsche Bank AG, ING Group NV, Lloyds Banking Group PLC, Oversea-Chinese Banking Corp. Ltd., Société Générale SA, State Bank of India, Sumitomo Mitsui Financial Group Inc., and Svenska Handelsbanken AB.
The banks using a recommended elliptic curve algorithm include: Barclays PLC, Oversea-Chinese Banking Corp. Ltd., PAO Serbank of Russia, Rabobank, and Société Générale SA.
None of the domains were identified as DNSSEC insecure or bogus.
All 68 domains from the 18 banks with signatures had SOA parameter timers that didn't follow best practices when used with DNSSEC signature validity periods. (Note that some SOA parameter checks may only be applicable if SOA timers are used for secondary server polling.)
These DNSSEC checks are part of a larger suite of tests which include over 80 measurements and tests such as for EDNS, TTLs, network counts, response times, DNS via TCP and IPv6, and more. Contact us for details about our full DNS audit service (with cited references and supplemental consulting).